Security Weekly 4: Attack on Cisco routers, a bug in AirDrop, the Arrest of crypto peers
“The life of three billion people was cut off on August 29, 1997. Survivors of nuclear fire called this day a ship. But they had to survive a new nightmare: a war against cars “
Not really. In 1997, developed the very first standard for WiFi networks (802.11b), Steve Jobs returned to Apple, came up with the PNG format, the computer beat the human chess. But the day of judgment did not happen, which is not, that is not. Machines are not so developed that it is arranged. They are far away from the real artificial intelligence, but this does not mean that nothing has changed in 18 years. Very much. If we treat the concept of “robots” extensively and beyond the limits of the Hollywood framework, now they are around us – darkness and local armageddons occur every day, here, and there. Thanks to the fact that robots, created to make people more comfortable to live, are increasingly out of control. Not themselves, it’s just that someone once did not create a very high quality, that’s all.
In today’s news digest, there are three topics about what mistakes people make when creating (software) robots, how other people exploit these shortcomings, and what people do for it.
Permanent backdoor through Cisco firmware upgrade
I think we already said that a modern router is a black box that (in most cases) works silently in a corner, and no one really thinks about what’s going on there? So, this applies not only to home devices but also to industrial ones. Specifically, a minimum of three Cisco router models found the potential for a backdoor installation, which, given the above, can go unnoticed for a very, very long time. The attack model for words is simple, in fact complicated: we get access to the router, fill in the modified firmware, get remote access to the device from anywhere and the ability to load additional plug-ins for (various atrocities).

- In fact, not everything is so bad. Researchers from FireEye identified three vulnerable models – Cisco 1841, 2811 and 3825. I understand that all three were released in 2004, are no longer sold and will soon cease to be supported by the manufacturer. The initial vector of infection does not exploit vulnerabilities in routers: the modification of the firmware supposedly occurred after accessing the device with the help of the default Password-password pair. Or with a unique password that somehow managed to find out. In itself, this situation is already a failure of corporate security, breaking through the security system a huge gap. Simple stealing login credentials would not interest anyone, but here it is the modification of the firmware that gives permanent access to the device and, most likely, to the corporate local network from the outside. The conclusion from this story is the usual: working with the sphere of info based safety, one can not be trusted. By the way, in all the Internet (at least in its IPv4 part) discovered less than a hundred infected routers.
Serious bug in the AirDrop data exchange system
So, about the revolt of cars. In the invented universe of the second Terminator (the third and further I deny), humanity first built Machines, which then, in fact, rebelled. And it built them so that, to mankind (well, more precisely to the warriors) it was convenient. Well, there’s a purpose of pointing laser pointer on the world map, fight viruses and so on. Here is such a greatly simplified, the model of a fairy tale is already embodied in reality. For a long time, the role of a person in managing gadgets, connecting to the network and exchanging data is reduced to pushing the buttons. Everything is done so that the response is loaded and ready for display, at the time or even before the device user has asked a question.

This, in general, is called progress, but there is one fundamental drawback: we almost do not control the interaction of our devices with the network. Take for example the excellent AirDrop feature. How many problems with the transfer of files she decided – do not think about “pairing”, “connecting an access point”, “authorization”, just chose the recipient within sight and sent the data. Vulnerability in this holiday of comfort was sooner or later to be found and yet found.
- A researcher from Australia Mike Daud showed how using AirDrop can remotely overwrite data on the victim’s device. All you need is to send a prepared package to your phone (or even to a computer running Mac OS X). When the user is received, they ask whether to accept the data or not, but it does not matter: the exploit has already worked (very similar to the StageFright vulnerability in Android). There is a limitation: the ability to receive data from all devices in the range of visibility should be enabled in AirDrop. But for convenience (!) Switch the mode of reception AirDrop can be without unlocking the device – that is, get an attacker access to the phone for a couple of seconds – and ready. Result: you can remotely install the application on your iPhone. Of course, it will be with the rights of a regular application and so simply will not be able to steal anything, but this is the story of other exploits, which usually perform the jailbreak.
The creators of the extortionist-encryptor CoinVault
While machines have not acquired their own intellect to do evil, people perfectly cope with this task. Not so often, as we would like, the disclosure of information that “someone has hacked someone” ends up with arrests of real cybercriminals. Let’s take the previous story: we found modified firmware for routers with a backdoor. Who modified it? What for? Unclear. Sometimes it may appear that the technology of anonymity on the Internet makes that part of the work for which the police are responsible is extremely difficult, almost impossible. Trojans-coders are one of the characteristic examples. To hide the management servers, Tor is used, to get a foreclosure – Bitcoin, like as you will not undermine at all.
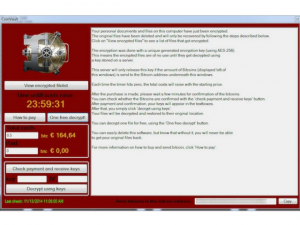
- The more pleasant is the news that two men were arrested in Holland on suspicion of involvement in the creation of the crypto lock CoinVault. Kaspersky Lab’s experts did a lot to make this arrest happen, carrying out their part of the work to investigate the technical side of the matter. CoinVault – not the most common extortionist, but a very revealing example of how difficult it is to dismantle such an attack. In a report published last November, it is described in detail how actively the cryptographic samples are trying to avoid analysis – if you run the Trojan in a virtual machine or on a computer with installed Wireshark and similar software, the “payload” execution is blocked.
After the publication of the November study, it seemed for a while that the organizers of the attack had stopped all activity until researchers from Panda Security shared a couple of new samples. Having collected a lot of indirect “evidence” the specialists of “Laboratory” were able to decipher the data of the victims of CoinVault without redemption. Suspects of co-ownership of CoinVault were also helped by the analysis of malicious code. At first, researchers found rows on “ideal Dutch”, while in most of the malware the standard is non-localizable bad English. Then, thanks to the technical information of the Dutch police (the unit of the National Hi-Tech Crime Unit), it was possible to withdraw the command server and identify those who controlled it.
Perhaps from this story, we can conclude that none, even the most perfect way to remain anonymous, while doing the crime, can be completely invulnerable. First, sooner or later, there is some way to counteract each new technology. Secondly, the capture of criminals is facilitated not so much by the vulnerability of technology as by the errors of the criminals themselves. And they will always be, it remains only to find and use them.





