How To Hack 50,000 Network Printers And Print Custom Text?
On November 9, 2018, a Twitter user under the pseudonym @TheHackerGiraffe “hacked” over 50,000 network printers and printed leaflets on them calling to subscribe to a certain PewDiePie’s YouTube channel. He says that in this way he wanted to contribute to the popularity of his idol, who is now fighting for 1st place in the number of subscribers on YouTube.
It is an interesting simplicity with which the hacker managed to access 50,000 printers. In the AMA question and answer session on Reddit, the hacker revealed the details of this hacking. It turns out that there is nothing difficult. Moreover, software tools are freely available on the Web for exploiting many vulnerabilities in old printer firmware. Unfortunately, literally, anyone can repeat this trick.
Messages on thousands of printers have caused quite a stir since they appeared on a variety of devices in different companies: from high-quality multifunction printers in large corporations to small portable receipt printers at gas stations and in restaurants, writes ZDNet.

This promotion is part of a big campaign that PewDiePie fans have launched. They are now agitating on social networks with all their might so that the Swedish blogger retains the leadership in the number of subscribers: at the moment he has 72.6 million subscribers, and in the back is a competing T-Series channel with 72.5 million subscribers.
Printers simply output a text message calling to subscribe to the channel.
Similar hacks
The current hacking of 50,000 printers is not unique. This happened repeatedly. For example, something similar was turned on March 24, 2016, by the hacker weev (real name Andrew Ouerheimer), who displayed racist and anti-Semitic messages on thousands of network printers. Interestingly, Ouerheimer joined the “white movement” in prison, where he was serving a 41-month sentence for a previous crime involving a computer hack.
In February 2017, this trick was repeated by another hacker Stackoverflowin, who printed silly drawings on more than 150,000 printers.
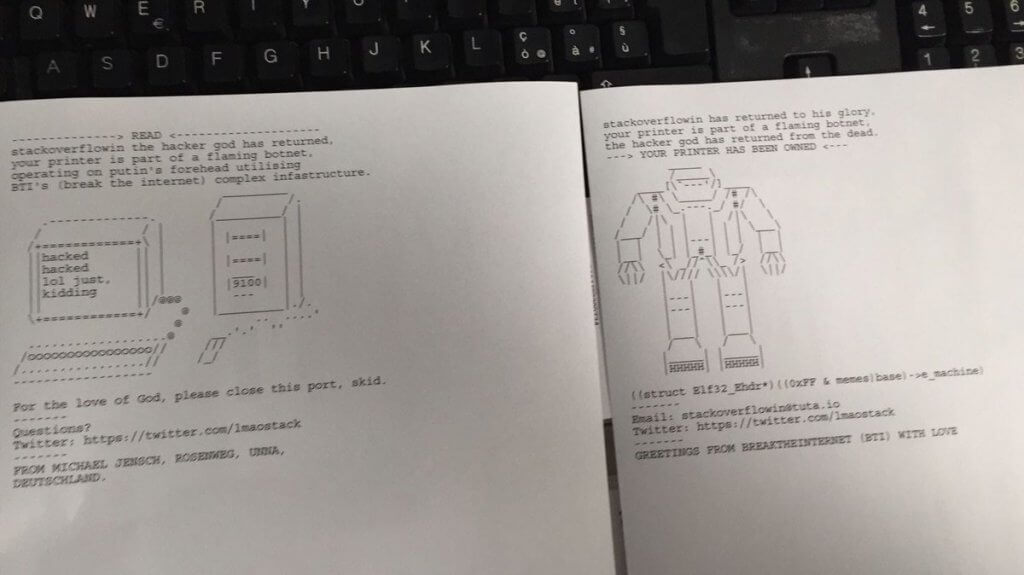
Technical details
As we have said, the technical side of hacking is not particularly difficult. @TheHackerGiraffe says that he did it out of boredom: “I was bored after four hours of playing Destiny 2 and I decided that I wanted to hack someone.”
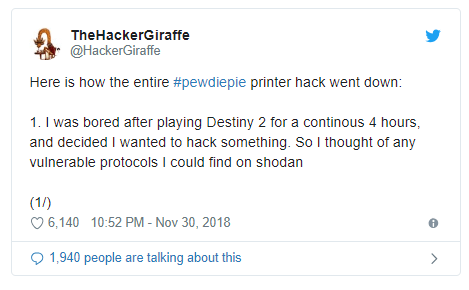
To search for vulnerable devices traditionally used search engine Shodan. It allows you to specify the port number and protocol – and get a list of network devices in which the port is open to the Internet, with the indication of IP addresses.
The latest attack was aimed at printers with open IPP ports (Internet Printing Protocol), LPD (Line Printer Daemon) and port 9100. Then a script is written to send PostScript file to the received IP addresses and the specified port, which is immediately accepted for printing.

In The Reddit AMA, the hacker @TheHackerGiraffe said that he sent messages only to 50,000 printers, although he could use a larger number: the search engine issued more than 800,000 non-patched printers with Internet ports using IPP, LPD, and JetDirect. But the hacker chose only 50,000 open port 9100 printers.
The list of vulnerable printers can be downloaded from Shodan. Then the hacker took the Printer Exploitation Toolkit (PRET) tool, the source code of which was freely published on the Internet and used it to connect to printers. By the way, PRET allows you not only to print a message, but also to gain access to the internal network, to files, and also just to damage the printer, among other things.
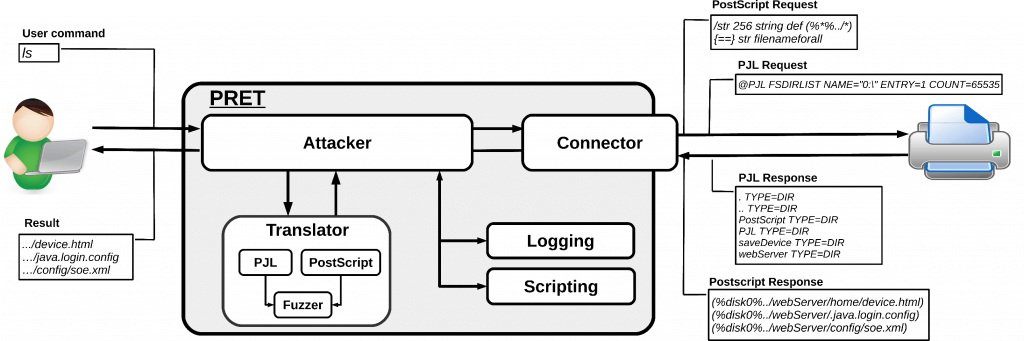
In January 2017, the program was laid out by a team of researchers, along with scientific work on the disastrous security of networked printers. In their work, they described in detail the six vulnerabilities in more than 20 models of network printers with old firmware. The tool is designed to test networks and search for vulnerabilities.
@TheHackerGiraffe has launched such a bash script. The script takes a list of printers with Shodan (potential_bros.txt) and cycles it to each PRET IP address with the commands specified in commands.txt
#!/bin/bash while read -r line; do ip="$line" torify ./PRET/pret.py $ip pjl -q -i ./commands.txt done < "./potential_bros.txt"
Content commands.txt:
print ./message.pdf display HACKED quit
Due to a large number of IP addresses, it is better to run the script somewhere on the server.

The attack in action, screenshot from the server. Photo: @TheHackerGiraffe
@TheHackerGiraffe does not consider its actions illegal because the printers are free to control via the Internet: “Imagine a large“ Print ”button on the Internet,” he says.
- Regardless of the goals of hacking and stupid use, the current incident says a lot about the protection of network devices (more precisely, the absence of this protection). As you can see, a huge number of users do not think about updating the firmware and do not follow the release of patches. However, it has long been known, now there has only been a clear demonstration of what this could lead to.
“People underestimate how easy an attacker hacker can use such a vulnerability to cause serious chaos,” wrote @TheHackerGiraffe. “.
However, printers are not the most interesting target yet. For example, Shodan finds about 190,000 open FTP servers.





