How to Detect a Suspicious Traffic in a Wireless Network with WifiBeat
In this article, we’ll talk about WiFiBeat, an agent that can send 802.11 frames to Elasticsearch, where we can analyze, build, and detect attacks. All this system is built entirely on Open Source OS.
Introduction
→ Official website of the utility
→ GitHub
- WiFiBeat allows you to work with a Wi-Fi adapter in monitor mode, create objects from JSON frames and send to the database of the analytical engine Elasticsearch. In addition, WiFiBeat can read frames from a PCAP file.
- The analysis of the collected information occurs in another free product from Elastic – Kibana visualizer.

- WiFiBeat officially works stably on Ubuntu 16.04, but, of course, it can be run on other distributions, but there may be difficulties with the dependencies and inconsistency of the versions of the libraries under which the utility was written. We will use 64-bit Ubuntu 16.04, which is connected to the USB Wi-Fi adapter TP-LINK TL-WN722N in monitor mode, to launch WiFiBeat.
- Elasticsearch and Kibana will be deployed on 64-bit Debian 9.
Installation of WiFiBeat
The installation process is described in detail on the GitHub.
Installing libtins
wget https://github.com/mfontanini/libtins/archive/v3.5.tar.gz tar -zxf v3.5.tar.gz cd libtins-3.5 apt-get install libpcap-dev libssl-dev build-essential libboost-all-dev mkdir build cd build cmake ../ -DLIBTINS_ENABLE_CXX11=1 make make install ldconfig
Install the missing packages in the system
apt-get install libyaml-cpp-dev libpoco-dev rapidjson-dev libtsan0 libboost-all-dev libb64-dev libwireshark-data build-essential libnl-3-dev libnl-genl-3-dev libnl-idiag-3-dev
Install Codelite for building WiFiBeat
apt-get install codelite codelite-plugins
Run code lite and create a new workspace
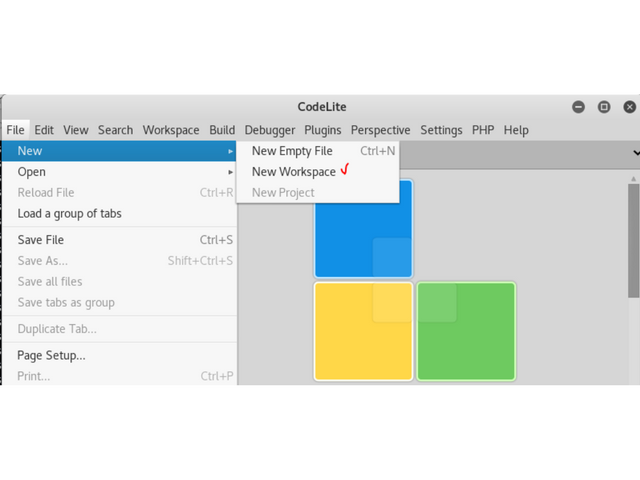
C ++ type

Remember the directory

When a workspace is created, go to the directory and download WiFiBeat and libraries with GitHub.
cd /root/WiFiBeat git clone https://github.com/WiFiBeat/WiFiBeat git clone https://github.com/WiFiBeat/elasticbeat-cpp git clone https://github.com/WiFiBeat/simplejson-cpp
Add all 3 projects to our workspace in codelite
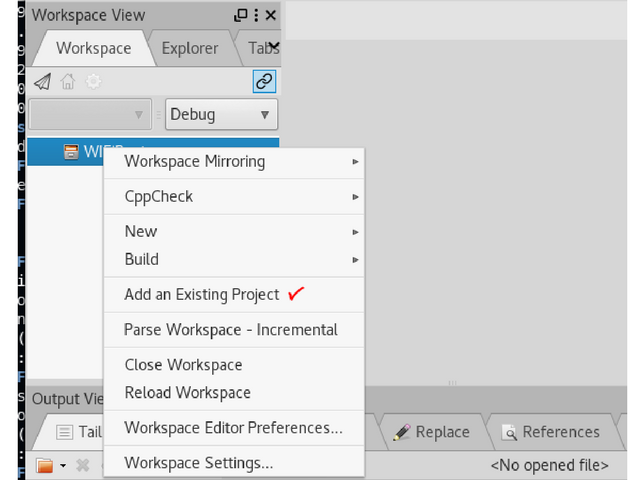

The result should be the following

After double clicking on wifebeat in the list of projects, it should stand out
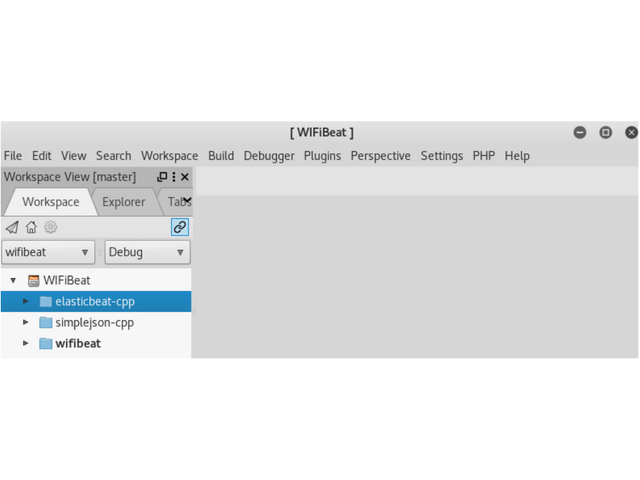
Right click on wifibeat choose to Build

Select the compiler if it was not selected, and again Build

If all the dependencies are installed in the system and you did everything correctly before that, then at the end of the compilation process you will see a message about no errors.
====0 errors, 2 warnings, total time: 00:01:13 seconds====
Customizing
- The installation process for Elasticsearch and Kibana will not be discussed in this article. On this subject, there is enough material on the network.
- We assume that they work on the machine with IP Address192.168.1.30 and WiFiBeat on the machine 192.168.1.31. Elasticsearch listens on HTTP port 9200 and does not require authentication.
- To the machine 192.168.1.31, We connected the Wi-Fi adapter and put it into monitor mode.
In the system, it is displayed as mon0. - From the directory with WiFiBeat, copy the configuration file to etc and edit it.
cp wifibeat.yml /etc vi /etc/wifibeat.yml
- This file is well documented, briefly go through the main options.
- We are going to analyze the traffic of one network operating on the fifth channel of the 2.4 GHz band.
- Therefore, I leave one entry in the interface settings. It is possible to analyze several channels at once and to set the listening time for each.
wifibeat.interfaces.devices:
mon0: [5]
- Deleting everything from the Output file section
- In the section with CPAP-filters, we will set the following
wifibeat.interfaces.filters:
mon0: type mgt
- The filters are specified as in Wireshark, and in this case, I indicate that I’m only interested in Management Frames 802.11.
These include:
- Authentication frame
- Deauthentication frame
- Association request frame
- Association response frame
- Reassociation request frame
- Reassociation response frame
- Disassociation frame
- Beacon frame
- Probe request frame
- Probe response frame
- Request to Send (RTS) frame
- Clear to Send (CTS) frame
- Acknowledgment (ACK) frame
- In the Local file and Decryption sections, we have commented out all the keys, we do not need encryption keys in my example and we will not read from the PCAP file either.
- In the Queues section, we will not change anything, and in the Outputs section, set the address and port of Elasticsearch.
output.elasticsearch: enabled: true protocol: "http" # Array of hosts to connect to. hosts: [ "192.168.1.30:9200" ]
- Save and go to the directory with WiFiBeat and the Debug subdirectory. There must be a compiled wife beat executable.
Running
- We launch Elasticsearch and Kibana on the machine 192.168.1.30. We are sure that the port 9200 (Elasticsearch) and Kibana (5601) are being listened.
- On the machine 192.168.1.31, we check that we did not make any configuration errors
./wifibeat -d
- You should see the parsing of the configuration file. If there are errors, wife beat will report the problem. If all is well, then we launch
./wifibeat -f
- The -f switch allows you to run wife beat, not in daemon mode. For us, it is more convenient.
- Now if you open Kibana and check the indexes, you should see that there is a new wifebeat index
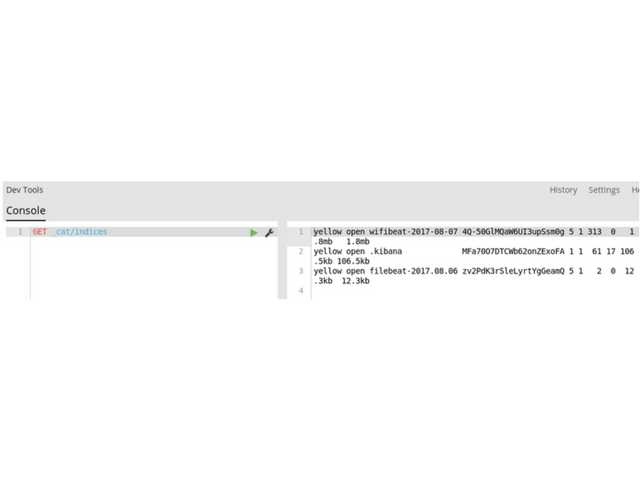
Let’s configure Kibana. Go to Management, Index Patterns

Create a new template


We mark it as the main

Now we import Dashboards and Visualizations that come with WiFiBeat

Choose the file kabana.json from the directory WiFiBeat/kibana
If the import was successful, you can go to the Dashboard tab and find the WLAN there

If you do not use filters in wifebeat.yml, it will look like this

With filters (in our case), we will not see data on Control Frames and Data Frames.
In addition to dashboards, we have new visualizations


Conclusion
Then, with the help of another component of the Elastic-X-Pack, you can configure actions to detect, say, a burst of de-authentication frames, which can mean a DoS attack or an attempt to get a handheld for brute force. In this way, you can assemble a system for detecting attacks on a wireless network.





