The First Botnet That Does Dot Fear To Be Rebooted!
At the end of April, IB researchers from Bitdefender LABS discovered a new version of the Hide and Seek (HNS) botnet, which became known in early 2018. It uses a custom P2P protocol and is the first botnet that “survives” even after rebooting the device on which it is fixed.
- We will tell you how HNS does it and how to protect from it the devices of the Internet of things.
Botnet “plays hide and seek” with IB specialists since January 10: at that time the Hide and Seek network consisted of only 12 devices. Most of them were IP-cameras produced by the Korean company Focus H & S, and their IP-addresses were spelled out in the code explicitly.
After the botnet “hid” and found himself only on January 20, but in its composition were already 14 thousand infected devices. After that, the botnet continued its active distribution and managed to infect about 90,000 unique devices. And now, in April, his new version appeared.
How the botnet works
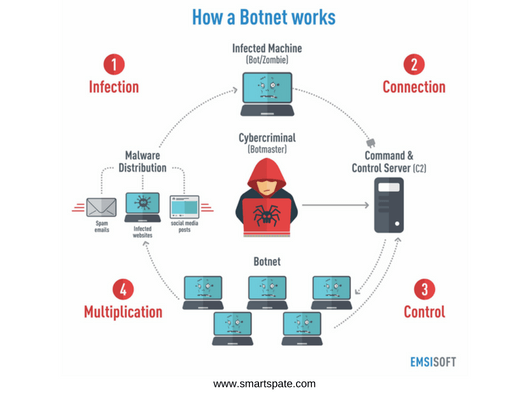
A new version of the botnet contains a number of improvements in the mechanisms of distribution. For example, he learned to exploit two more IP camera vulnerabilities (more here), which allowed to increase the access rights in the system and gain control over the device. In addition, the HNS can define two new types of devices and access them through logins and passwords (using the list of default passwords).
The mechanism of distribution of HNS reminds how the network worms “multiply”. First, the bot generates a list of random IP addresses to select victims. Then it sends an SYN request to each host and continues to “communicate” with those that responded to the request on ports 23 2323, 80 and 8080. Once the connection is established, the malicious user searches for the “buildroot login” message and attempts to authenticate with the predefined credentials. In case of failure, HNS applies a dictionary search to the hardcoded list.
- Once connected, the botnet determines the target device and selects the appropriate compromise method. For example, if the bot is with a victim on the same LAN, it configures the TFTP server, allowing the target to download the malware sample directly. If the victim is “located” on the Internet, the botnet tries various methods of remote delivery of the “malicious parcel”. All exploits are preconfigured and stored in a memory cell with a digital signature to prevent unauthorized access. The list of methods can be updated remotely and distributed among infected hosts.
IB researchers found that the botnet in the arsenal has ten binaries compiled for different platforms: x86, x64, ARM (Little Endian and Big Endian), SuperH, PPC, and others.
And to securely gain a foothold in the system, after successfully infecting the target device, the bot copies itself to /etc/init.d/ and activates the autoload function along with the start of the OS (interaction with the victim occurs via Telnet since the binary copying to the init.d directory requires root -rights). Then, HNS opens a random UDP port that cybercriminals will need to connect to the device.
Other large botnets
One of the most famous IoT bots is Mirai. Just like HNS, this botnet looked for IoT devices with open Telnet ports. Authors Mirai, fans of Minecraft and anime (Mirai in Japanese translation means “future”, in honor of the manga “Diary of the Future”), in 2016, conducted several powerful DDoS attacks on sites, servers providers (in September and October) and infected about 300 thousand IOT-devices (here you can find a detailed analysis of the sources Mirai).
Another well-known case is Hajime (in Japanese it means “beginning”). This botnet captured 300 thousand IoT-devices using brute-force attacks. Hajime’s attacks were mostly aimed at digital video recorders, webcams, and routers. According to the research of Kaspersky Lab, the botnet basically infected devices from Vietnam (20%), Taiwan (13%) and Brazil (9%). At the same time, Hajime “deliberately” avoided private networks (including the networks of the US Department of Defense, Hewlett-Packard companies, General Electric and others).
How to protect yourself
According to representatives of Bitdefender, the botnet of HNS is still at the “growth stage”. His operators are trying to capture as many devices as possible. Therefore, attacks with his participation have not yet been conducted. But there is a possibility that in the near future hackers will add “combat teams” to binary files.
To protect the Internet devices of things from attacks of HNS and botnets in general, IS specialists from Trend Micro recommend following simple and rather trivial steps:
- Change the password of the IoT device by default to a more complex one (everything is as usual: a minimum of 15 characters, a different case of letters, plus numbers and signs);
- Regularly install updates, especially those related to security;
- Use software solutions for network protection, traffic encryption, etc.
These simple methods will protect against many malicious machines that “hook up” in their ranks the devices of the Internet of things.





