Security Weekly 11: Attack on Dyn Servers, Life of Fake Technical Support, Vulnerability in Linux
The main news of the week was the attack on DNS servers of Dyn company last Friday. A powerful DDoS attack began in the morning in the US time, took place in two stages and for a few hours led to access problems or to the complete inaccessibility of many Dyn client sites.
Among the victims:
Virtually all of these sites worked, but the DNS servers that served them were unavailable, from the user side, the inability to translate the name of the website into an IP address looked the same as if the service had gone offline entirely. As usual, the inaccessibility of a large social network led to glitches and a drop in sites that had nothing to do with it at first (for example, the hunger code for Twitter elements prevented the download of The Register site.

Later, the assumptions about the source of the attack were confirmed – it was a bot of IoT-devices Mirai, previously noted a massive attack on the blog of Brian Krebs. The Mirai code was posted openly, which led to a noticeable increase in the number of victim devices. There were already a lot of them: 380 thousand according to the original “owner” of the source code.
The term “hacking” to susceptible devices is not entirely applicable: in most cases, exploited by common vulnerabilities and wired passwords. OEM-manufacturer Xiongmai, partially responsible for unsafe firmware devices, even launched a US revocation campaign, which, incidentally, applies only to several thousand IP cameras. The rest are released recommendations and firmware updates. The problem is that hardly all device owners will update the devices.
The subject of the vulnerable Internet of things continues to evolve, despite the fact that the IoT era itself has not even really come about. I hope that the problem of vulnerable-by default devices that are either difficult or inconvenient to update will begin to be resolved. Attacking Dyn will also be a useful experience in enhancing protection against DDoS. It is necessary: according to the company Level3, that in the DDoS-attack involved only about 10% of devices from a botnet the size of half a million.
Microsoft warns about a fake Security Essentials antivirus with built-in telephone fraud
Experts from Microsoft raised this week an interesting topic of telephone cyber fraud. Typical for Western countries.
The “attack” is as follows: you are allegedly called from Microsoft support, and representative telling you that your computer has a security problem (it is infected with a virus or some other fake story), and offer to solve the problem remotely. Further variants are possible – both with malware downloading and with a remote connection to your desktop. Or with payment for the “removal of the virus”, or for installing a counterfeit software.
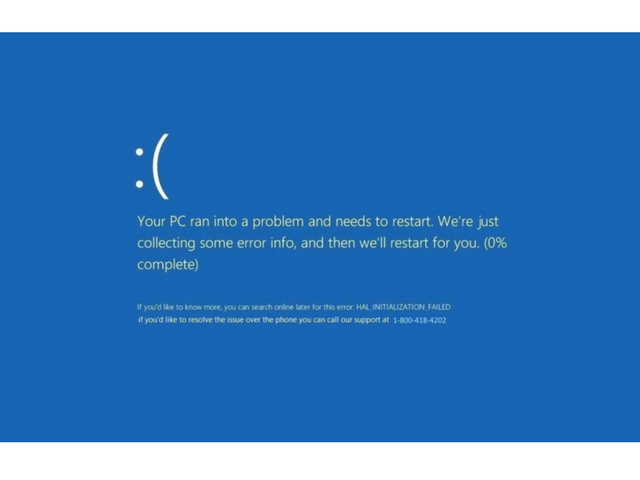
In this case, everything works a little differently: there is a fake Microsoft Security Essentials installed on the network. The calculation is that in Windows 8 and 10 this antivirus was replaced with Windows Defender, but someone could remember the old name and “find” the program on the network. After installation, the user is shown a fake blue screen of death with a phone “tech support”, further processing of the victims is transferred to offline. Our colleagues from the states checked – on Monday the phone worked, and there they claimed that they were absolutely certified and authorized. Usually, somehow these phone scammers try to sell something to the user.
As a recommendation, Microsoft experts recommend a strange one: to be able to distinguish a real BSOD from a fake one. Not the best advice for the target audience of such scammers. It is easier to block attempts to infect immediately, the more reason is enough: the lack of a certificate, and rectilinear attempts to disable the task manager.
Vulnerability in the Linux kernel allows you to get root privileges locally
The “Dirty Cow” or Dirty Cow vulnerability was named because the Copy-On-Write mechanism is involved. The cow is used to optimize resource consumption, if different processes request the same data set (for example, on a disk). In a normal situation, you would need to create a copy every time, but in the case of a COW, a copy is created only when the process tries to change the information. An error in the Linux kernel allows you to create a race condition, the result of which will be writing to the original file, and not to a copy, even if the initiator of the record does not have this right.

Interesting details are on the page of the committed fix. Linus Torvalds writes that he tried to fix the problem 11 years ago, but then there were some difficulties with the systems on the S390 architecture. Perhaps then they did not pay attention to this since the practical possibility of a “race condition” depends also on the system’s performance, and at that time the attack seemed not realizable. As a result, the vulnerability exists in all versions of the Linux kernel since 2007 and is currently not patched everywhere. All would be fine, but there is evidence of an exploit “in the fields”.





