Overview of Juniper Networks security solutions against DDOS attacks at the application level
In the past few years, Distributed Denial Of Service (DDoS) attacks evolved from relatively simple (flood) attacks into fairly complex and multistep attacks. Together with the traditional high-level attacks, which send massive amounts of traffic to overload the server, the business has also faced targeted attacks. They use a relatively small amount of traffic, aimed at applications that process huge amounts of data. And these attacks are not detected by traditional protection solutions from DDoS.
The Juniper Networks DDoS Secure solution provides fully automated DDoS protection for Internet services, using a behavioral approach to detecting and repelling DDoS attacks. The solution provides protection against high-level attacks, as well as advanced “low-and-slow” attacks at the application level. By correlating input risks and response, DDoS Secure is able to detect “invisible” attacks, which are designed to bypass signature protection systems.
First about DDoS
- The first distributed attack of DDoS type took place in 2000 and was aimed at Amazon, eBay, and other e-commerce sites. As a tool used botnet from a variety of PCs that generated a huge number of requests and loaded servers serving e-commerce portals, so much that they could no longer handle user requests. The total damage from the attacks is estimated at about $ 1.7 billion.
- Since then, DDoS-attacks have evolved very much: from a primitive tool that uses attacks with a large amount of traffic to reload web servers, to complex attacks of the application level designed to attack the strategic business resources. In 2012, there was a series of such attacks against the banking industry, with the goal of financial fraud. Sectors of education and e-commerce have also become targets of cyber criminals.
The Internet and social networks have made information weapons that can be used against users. This means that cybercriminals still have access to a lot of cheap botnets and free software such as Low Orbit Ion Cannon (LOIC), which are easy to use and can disable the application infrastructure of most companies.
The cost of one hour of DDoS attack was about $ 5, the week of continuous DDoS attack is about $ 260, and the month is only $ 900 (see Figure 1).

The ways and motivations for using DDoS have also evolved. This type of attacks was more often used by groups of “hacktivists” such as Anonymous for social protests and organized criminal activities, inflicting financial damage on attacks on specified websites and web services. In addition, DDoS attacks play a big role in sophisticated hybrid attacks on organizations for which the Internet plays a critical role. Hybrid attacks involve the use of DDoS techniques in order to confuse the teams of IT and IS specialists and effectively divert their attention from more vulnerable places in the defense.
- Not only tactics but also motives for DDoS attacks have become somewhat different over the past couple of years, from “hacktivism” to financial exploits and fraud, as well as politically motivated attacks and attacks of social protest. Some experts even stated that DDoS-attacks “are collected under the umbrella of civil disobedience.”
- 2013 showed that DDoS attacks reached a new level and led to even more references in the media. While many companies continue to believe that their websites and application infrastructure are adequately protected against cyber attacks, others are already prepared to defend against the more complex structure of DDoS attacks. According to an independent study, 64% of IT professionals (having more than 10 years of experience) stated that the power of cyber attacks is on the rise, while only 25% said they have the ability to take appropriate countermeasures. Only 22% of IT managers making decisions have already implemented protection against DDoS.
Constantly changing landscape of DDoS-threats
Escalation of DDoS-level application attacks
DDoS attacks of the application layer are today one of the most widespread and destructive forms of cyber threats. Simple DDoS attacks with a large amount of traffic still cause problems, but they are easy to detect. With the proper organization of defense, the risks of these attacks are reduced to zero. A new type of application-level DDoS, codenamed “low-and-slow”, however, is much more difficult to detect and reflect, which is a real threat to business.
2012 has shown a sharp jump in DDoS attacks such as Layer 7. These attacks are insignificant because they give their traffic for legitimate. Layer 7 attacks or application tiers are more likely to focus on vulnerabilities in the application code itself than to apply frontal attacks to achieve the desired results. The goal of most application-level attacks is well-known software that uses HTTP, HTTPS, DNS, and VoIP (Session Initiation Protocol or SIP). Like flood attacks, L7 attacks require very little cost from cyber criminals. It is possible to paralyze large websites from one laptop by sending 40 to 60 identical requests per second (abbreviated PPS, or packets per second). At the same time, in flood attacks, it is sent from several hundred or thousands of PPS to millions. External legality is what makes L7 attacks common and extremely difficult to detect and block.

Application-level attacks can not be detected by a security system because they use the weak side of detection technology, which uses the principle of network flow and the methodology of threshold values. RUDY (R-U-Dead-Yet) and Slow Loris are two types of application-level attacks that target the HTTP protocol. Attackers try to run many queries that are difficult to maintain, exhausting application resources and quickly paralyzing the website.
Some time ago, hackers began to use the attack of DNS-amplification (reflection). Its essence is that a hacker sends a short request to a vulnerable DNS server that responds to it with a much larger packet. If you use the IP address of the victim’s computer (IP spoofing) as the source IP address, the vulnerable DNS server will send a lot of unnecessary packages to the victim computer until it completely paralyzes its operation.
DNS servers are an attractive prey, because they are usually very large, operate on a broadband Internet channel, and can not be so easily listed in the black list.
Hackers use DNS by substituting the target address and sending small requests to the DNS server, which response to these false requests in 10 ~ 1000 times with a large amount of traffic, thereby bombarding the victim with a massive wave of traffic. Taken separately, these DNS queries are legitimate, as are the response data; Nevertheless, due to camouflage, an attacker can remain anonymous and manage publicly available DNS to repel attacks and increase their power.
- Using such methods of attacks in 2013, a small group of criminals was able to generate the largest DDoS attack in history, reaching a continuous traffic flow at 300 Gbit / s. Hackers attacked spamhaus.com, an organization that publishes “black” lists of spammers on the Internet.
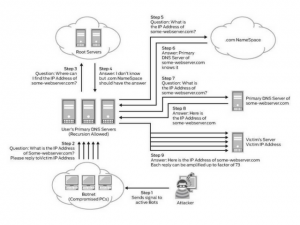
Alternative form of DNS attacks can result in security breaches, as recently happened at the University of California in Sacramento, when about 1800 records were stolen. Hackers were able to crack the university DNS server. But not only universities are at risk. The game, financial, the retail online industry is also vulnerable to such attacks. The anatomy of the DNS-gain attack is shown in Fig.3

The distracting DDoS attack, which is a much more insidious type of multi-vector attacks, uses large-scale DDoS as a tactical diversion of IT personnel, while cyber criminals steal data or financial assets. Banks and financial institutions are most often exposed to this type of attack. A public example is a cyber attack that occurred at the Bank of the West4 in December 2012. Knowing that the IT team will be on vacation, hackers have correctly chosen the time and context of the goal. First, the bank was subjected to DDoS attacks, and while bank employees and IT personnel tried to stop a powerful flow of traffic to their servers and keep the stability of online services, cyber criminals successfully stole $ 900,000.
- The recent distracting DDoS attack on the online currency Bitcoin6 illustrates the permanently transformable essence of DDoS. In this case, cybercriminals used DDoS attacks as a “smokescreen” to implement an attack on Bitcoin DNS records. Hackers could create another IP address in the current DNS record for the Bitcoin online chat forum. By inserting these malicious machine addresses into a normal everyday DNS mechanism, hackers transparently redirected user traffic to a server owned by attackers. Once a user entered his account on a compromised machine, hackers wrote down his account name and password, which could later be used to empty the wallet of that user.
An attack to steal passwords against Bitcoin users could be detected, but this was prevented by a “smokescreen” created with a DDoS attack that violated availability, while DNS address records changed.
- Attacks level of applications is increasingly directed against online banking online stores. These attacks are often hidden in encrypted (HTTPS / SSL) traffic and they remain invisible to traditional solutions. As an example, such an attack can be launched by the “add to cart” function on the web server, generating more traffic than it can handle applications, overloading the site and generating error messages for end users who are trying to make online purchases. These attacks are not detected until it is too late because they use legal traffic channels to penetrate web servers and applications.
“Zero-day attacks” are megatrends of DDoS, they are aimed at the newest discovered vulnerabilities in web applications, rather than the avalanche data flow. A huge number of web applications are now launched on mobile devices (remember the trend BYOD), which puts the company at great risk of DDoS attacks of “zero days”.
Impact on business
Currently, the vast majority of IT and information security professionals are aware of the business risks that cyber attacks carry. At the same time, they are not properly prepared. According to a Ponemon Institute survey conducted in February last year7, 60% of IT professionals responded to a questionnaire that DDoS attacks are the most serious type of attacks that companies experience. The damage caused by a DDoS attack can have a huge impact on the business, regardless of its size.
As companies increase their presence on the Internet and thus extend the “front line” on which an attack can be conducted, the downtime of web servers or applications due to DDoS attacks is a real threat. Businesses rely on the continued availability of their web servers and applications, so a few hours of downtime can lead to disaster. They must ensure the operation of web services without any interruptions in the 24x7x365 mode. The stability of applications is a critical requirement for these businesses.
Downtime not only leads to losses and scaring away customers, they also negatively affect the brand’s value and reputation. In the financial services industry, cyber criminals use stealing confidential data and financial fraud. In the education and health sector, the main interest lies in access to student information, electronic medical records, and theft of sensitive confidential data, which can lead to major lawsuits and terrible consequences for people to whom information is stolen. Failures in the operation of air ticket sales sites and online stores lead to lower profits and loss of reputation. A DDoS attack can be followed by financial losses that are hard to recover.
- Statistics of DDoS-level application attacks are alarming. Gartner estimates that 70% of all threats are targeted at the level of Web applications. The Ponemon Institute study found that the average annual damage from a DDoS attack is estimated at $ 3.5 million. Another recent Forrester study estimates the average financial cost of $ 2.1 million for every 4 hours of downtime and $ 27 million for 24 hours of downtime caused by DDoS attacks. Forrester indicates that the frequency of attacks in all industries is approximately equal to 1 time per month, while in the financial sector this happens once a week. Based on publicly available estimates of damage provided by organizations that have been attacked, financial companies suffered an average loss of about $ 17 million for each incident in 2012. And while financial organizations most often attack, the Forrester study showed that government agencies, on average, Are subjected to more prolonged attacks. This is due to the fact that financial institutions, as a rule, use better protection from cyber attacks.
Despite this alarming statistics, less than 25% of companies have implemented protection solutions against DDoS …
The need for a dedicated local DDoS solution
Reflection of avalanche attacks at levels 3 and 4 is traditionally performed in the cloud with the help of a solution that inspects reverse traffic. These attacks, requiring a wide channel, are easily detected and reflected by the service provider. In fact, customers may not even notice any problems. There are, however, many environments where, mainly for security reasons, data simply can not leave private networks. In addition, application attacks of the “low and slow” type can not be reflected in the cloud, since these attacks usually do not consume a lot of traffic and are hidden in legitimate traffic.
Reflecting these attacks requires a separate local solution in the corporate data center. A dedicated DDoS solution is required for a variety of reasons:
• Perimeter security system including firewall, NG firewall, and separate intrusion prevention systems are not well suited for protection against DDoS attacks since well-technically prepared attacks can quickly overflow the connection status table and paralyze the firewall or IPS, exposing the entire network to risk.
• Firewalls and IPS systems can in themselves become targets for a “failover” attack, requiring protection.
• Firewalls and IPS systems can not withstand more sophisticated application-level attacks because these solutions are designed to skip those protocols that are used during these attacks; Every hacker knows that the firewall usually skips HTTP and HTTPS traffic because most systems require such access for the appropriate connection with the web service.
Limitations of traditional solutions for repelling DDoS attacks
Traditional solutions for detecting DDoS attacks are limited in their capabilities, they are able to control only network telemetry, such as NetFlow, which does not carry application-level attributes and leaves a big gap in detecting modern application-level attacks. In addition, all these solutions provide signature detection and reflection of attacks in the “on premises” mode, which is not effective against unknown zero-day attacks. Further, such solutions evaluate only the input traffic based on the threat signature base, leaving security vulnerabilities for the passage of malicious traffic. One example is the DNS gain attack.
In addition, traditional solutions are not able to distinguish between legitimate and generated engine (malicious) traffic. Thus, the system must be manually configured to determine the high / medium / low thresholds at which traffic should be blocked. This approach leads to a compromise between the low threshold of false positives and aggressive defense.
If the threshold is set too high, this creates a false positive triggering problem, which results in blocking large amounts of legitimate traffic. If the threshold is underestimated, then potentially malicious traffic will be resolved, which will lead to hacking. The lack of security tools at Layer 7 and the inability to monitor protected resources make traditional DDoS solutions ineffective against modern attacks that occur outside the boundary of the signature perimeter. The static threshold does not meet the protection requirements. There is also an administrative problem associated with supporting a set of signatures and manually setting the threshold.
In short, providing a full range of protection against modern DDoS attacks requires a separate solution with a short wait time located locally on the perimeter of the data center. This solution evaluates the performance of each application, from layer 7 to the network resources required to ensure their availability, monitoring both inbound and outbound traffic. This is the most effective approach to preventing known and unknown attacks that distinguish legitimate and malicious traffic and minimize false positives. In this case, you do not even need to manually adjust the alarm threshold, which was always necessary, and in fact, it creates a constant operational load, and always lags in comparison with the real changes in the traffic pattern. This innovative heuristic approach is described in more detail below.
Juniper DDoS Secure – protection against DDoS attacks for business critical applications
Juniper Networks released DDoS Secure, which passed the “battle test” and showed high results in the detection and reflection of DDoS attacks. For today, the product has helped to avoid damage worth about $ 60 billion for companies working in the field of mass media, online retailers, online games, finance, education and government agencies.
- In contrast to traditional solutions, DDoS Secure uses non-signature technologies to detect and repel an application-level attack. The program inspects all incoming and outgoing traffic on the perimeter of the data center and monitors application performance with each incoming client request. Before using the threshold method or setting to repel attacks, DDoS Secure uses a special algorithm, CHARM, to quantify real-time risks associated with two-way traffic. The product analyzes the resources of the target application when the latter arrives under attack. If an application is attacked, it raises the CHARM threshold required to access applications, blocking the riskiest traffic. By correlating incoming risks and outbound responses, DDoS Secure is able to detect invisible attacks that typically bypass traditional signature protection solutions from DDoS.
Innovative architecture DDoS Secure uses a “feedback” process to analyze the full cycle of incoming packets and the response that was sent back to the requesting party.
DDoS Secure is self-learning and does not require setting or defining a threshold value. It monitors how the application reacts and analyzes each attack. This innovative heuristic approach allows technology to determine how normal traffic and a normal response from the application should look. When a new attack occurs, DDoS Secure updates the algorithm to include the characteristics of the new attack, creating a highly intelligent defense system from DDoS that includes dynamic updates. In the event of a DNS gain attack, DDoS Secure applies an intelligent approach to the DNS resource in order to repel the attack before it paralyzes the DNS server. Special DDoS Secure filters filter out periodic DNS system queries for the same information, thereby preventing the attack of DNS gain and protecting the target of malicious users from malicious requests that affect their availability.
In essence, the system distinguishes real user traffic and traffic generated by the machine. This approach guarantees the passage of legitimate traffic and blocking attacks before they cause harm. This is critical during the period when the servers are under high load, for example, during the Christmas holidays, when any interruptions in access to the server due to false positive triggering can lead to a drop in profits. Many cyber criminals now combine these new sophisticated DDoS attacks with traditional “avalanche” attacks; At the same time, DDoS Secure is able to detect and prevent both types of attacks.
DDoS Secure can be installed as a 1U physical device or a virtual machine. Because the solution correlates incoming and outgoing information for risk assessment, rather than using a predefined threshold, false positives are limited, making management simple and easy to deploy. In addition, BGP integration allows the solution to work with a cloud-based security solution to combat large-scale “avalanche” attacks.

More related information:





