A New DNS Protocol Was Invented by Apple, Cloudflare and Fastly
The Cloudflare, Apple and Fastly have announced the development of a new DNS standard that separates IP addresses from requests. Oblivious DNS over HTTPS (ODoH) is open source.
The Common Domain Name System (DNS) maps domain names in use, such as cloudflare.com, to IP addresses and other information required to connect to that domain.
- DNS requests are sent in clear text. This means that a third party may appear on the network path between the device and the DNS resolver, who will see both the request with the hostname and the IP address of the gadget.
To protect DNS from intruders, the DNS over HTTPS (DoH) and DNS over TLS (DoT) standard was developed. Both protocols prevent interception, redirection, or modification of requests between the client and the transformer. Client support for DoT and DoH is growing, with the latest versions of Firefox, iOS and more. However, for now, Cloudflare remains one of the few providers offering a public DoH/DoT service.
- The key component of ODoH is a proxy that is not associated with the target resolver. The protocol was launched with the support of proxy partners including PCCW, SURF and Equinix.
ODoH adds a public key encryption layer as well as a network proxy between DoH clients and servers like 1.1.1.1. The combination of these two additional elements ensures that only the user has access to both DNS messages and their own IP address at the same time. The target decrypts client-encrypted requests through the proxy. Likewise, the target encrypts responses and returns them to the proxy. In this case, the target sees only the request and the IP address of the proxy, decrypting them using the DNSSEC key. The proxy server does not see DNS messages and cannot identify, read, or modify either the request sent by the client or the response returned by the target. The client can select and change his proxies and goals at any time. Thus, a successful attack can only be realized if both the proxy and the target are compromised.
The added encryption is “end-to-end” between client and target and is independent of the connection-level encryption provided by TLS/HTTPS. Proxy functionality requires two separate TLS connections. Specifically, the proxy terminates the TLS connection from the client and initiates another TLS connection with the target. ODoH additionally encrypts messages between the client and the target, so the proxy doesn’t have access to the content of the message.
Clients transmit encrypted requests to the proxy server over an HTTPS connection. Upon receipt, the proxy server forwards the request to the specified target. The target then decrypts the request, issues a response by sending the request to a recursive transformer like 1.1.1.1, and encrypts the response. The encrypted request from the client contains an encapsulated key material from which targets obtain a symmetric encryption key for the response.
Along with the increased security and performance of the PCCW core WAN, which can be accessed on demand via Console Connect, the performance of proxy servers on the network is enhanced by Cloudflare 1.1.1.1 resolvers. This model completely decouples client proxy from resolvers for the first time,
Michael Glynn, VP of Digital Automated Innovation at PCCW Global
The protocol is supported by the ESNI (Encrypted Server Name Indication) TLS extension, which will allow you to transmit the requested host ID in encrypted form. In 2018, it was developed by Mozilla, Cloudflare, Fastly and Apple.
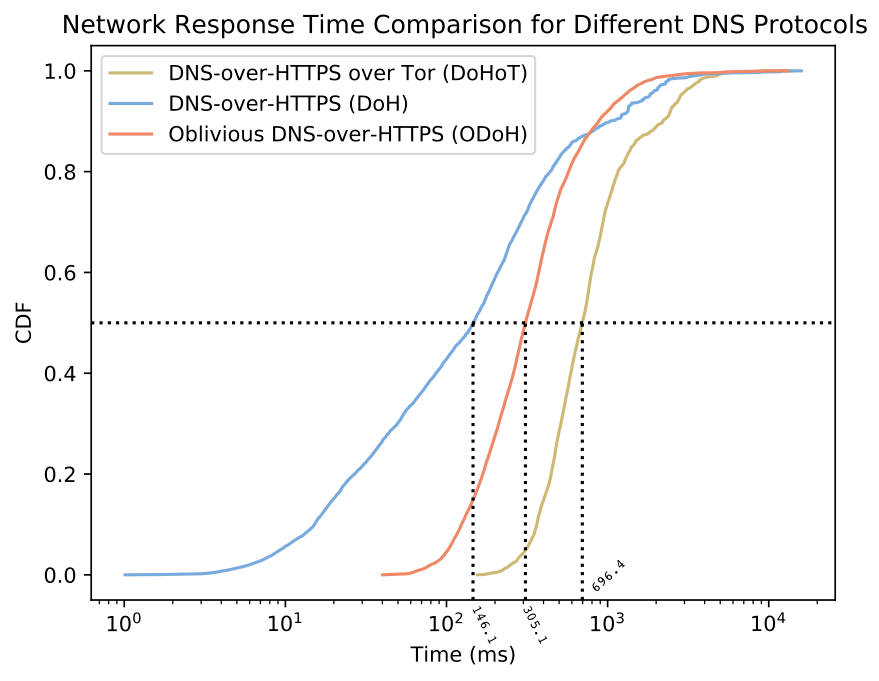
The diagram below shows the cumulative distribution of DoH, ODoH, and DoH request/response times over the Tor network.
- Compared to other privacy-focused DNS options, ODoH cuts query times in half or more.
Open source ODoH implementations are available in Rust, odoh-rs and Go, odoh-go.





